Cloud computing is a blessing for the modern age in terms of its agility, unlimited storage capacity, excellent accessibility, and improved collaboration to execute business functions seamlessly. Managing huge chunks of data is no longer a nightmare for businesses that adopt the hybrid cloud environment. However, security threats are the one critical concern this trending technology brings forth. Partnering with a professional hybrid cloud development company can let you effectively manage cloud infrastructure security challenges to avail yourself of the best technology.
What we cover in this blog
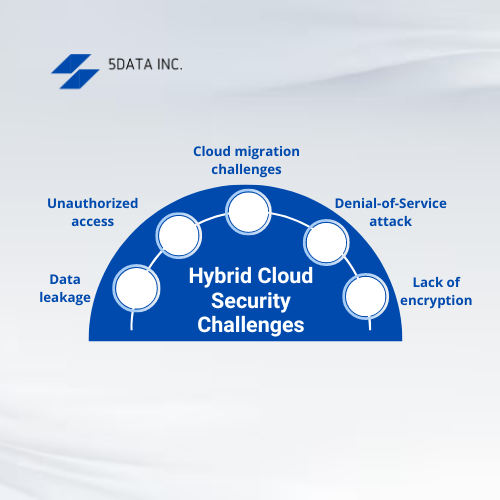
Common Hybrid Cloud Security Challenges
A hybrid cloud environment amalgamates the private cloud environments and the public cloud services to derive the best of both worlds. Nevertheless, security professionals warn against the following security breaches evident in a complex hybrid cloud environment.- Data leakage: Leakage of sensitive information is a potential risk in a hybrid cloud model, public and private cloud. Cloud security best practices are essential to protect data and prevent data breaches.
- Unauthorized access: Insecure APIs can penetrate unauthorized access in hybrid cloud environments. Public clouds and hybrid cloud architectures are more prone to unauthorized access than private cloud resources.
- Cloud migration challenges: Changing service providers or migrating from a public cloud environment to hybrid clouds can bring about various issues like misalignment of SLAs, network connectivity breaks, and more.
- Data loss due to DoS attack: A Denial-of-Service (DoS) attack is commonly caused due to high traffic online, resulting in the loss of important data at times.
- Lack of encryption: The standard data protection risks also apply to hybrid cloud environments. The data movement between clouds makes hybrid infrastructure fragile and subject to significant hazards. If suitable encryption is not provided, the connecting architectures are the main source of theft or altering events.
Hybrid Cloud Security Strategy And Best Practices
Cloud adoption statistics from zippia.com reveal that the share of corporate data stored in the cloud environment has risen from 30% in 2015 to 60% in 2022, signifying the increasing trend in cloud adoption over the past few years. The numerous benefits of cloud computing are responsible for this rise, which is expected to increase in the coming years. But the challenge lies in offering hybrid cloud security to the sensitive data. Here are some best practices to mitigate security risks that organizations can follow with the guidance of a reputed hybrid cloud development company.1. Aligning with the shared responsibility model
It is important to understand the role of the customers and cloud providers in maintaining cloud security in a multi-cloud environment. The level of shared responsibility varies with the cloud service delivery model used, which could be IaaS (Infrastructure as a Service), SaaS (System as a Service), or PaaS (Platform as a Service), and the deployment models, which could be Private cloud, a Public cloud or a Hybrid cloud. Cloud service providers normally do not reveal information about their host platforms to prevent access to hackers. The customer is entirely responsible for the data and information stored in the cloud, cloud-connected devices like laptops and mobiles, and the accounts maintained. The cloud services provider is responsible for the physical hosts, physical network, and the physical data center. It applies to multi-cloud environments that consist of SaaS, PaaS, and IaaS models. In an on-premises network infrastructure, the customer is responsible for security monitoring. However, maintaining the applications, operating system, and network controls lies entirely with the cloud provider in the SaaS model and with the customer in the IaaS model. In the PaaS model, maintaining the applications, OS, and network controls is a shared responsibility between the customer and the cloud provider. It is a good practice for enterprises to review the policies of the hybrid cloud development company before partnering with them to understand the level of responsibility shared between them to prevent mishaps in the future.2. Using automation in security checks and remediation
With the constantly changing cloud footprint and the numerous updates to the cloud infrastructure coming up, the risk of misconfiguration of cloud resources is huge with every single update. When a hacker tricks a data system into trusting him with access credentials of a web application firewall to decrypt the data, there is every possibility of a data breach. The remedy lies in using automated security checks that flag anything suspicious in the cloud systems. Proper endpoint detection response tools for network and endpoint security and anti-malware, VPNs, and intrusion detection software can build a strong defense strategy. It would also be helpful to use automated remediation that works to reconfigure the cloud resources that cause violations and fix the vulnerability automatically without human intervention. These automated measures are far more effective than manual compliance checks in maintaining cloud data security.3. Implementing operational security procedures in a hybrid environment
Cloud service providers should adopt sufficient security measures to ensure cloud data protection. Some cloud security best practices to secure virtual servers in hybrid environments, public and private clouds, include the following-- Availability of the host firewall should be restricted to minimum necessary ports.
- Unused services should be disabled. Only essential services like print, FTP, and database should be used.
- Use passwords for role-based access, like for SELinux. Do not allow authentication through password at the shell prompt.
- Private keys should be safeguarded to prevent users from accessing public cloud hosts.
- Virtualized images should be protected from unauthorized access and have no authentication credentials to decrypt them except a key.
- Decrypted keys should be restricted to the usage time and isolated from the cloud.
- Essential services like print, FTP, and database should remain while disabling all other unused services.
- Standard encryption of cloud data helps to maintain data security.
- Ensure safe browsing for PCs connected to the internet so that the non-HTTPS certified websites are filtered out from being accessed.
- Ensure periodic checks for the audit trail logs to detect any suspicious activity.
The Best Cloud Service Provider For Your Cloud Computing Needs
5Data Inc. is the best software application development company that utilizes the power of data analytics to boost your business with a digital transformation. The mobile development company also specializes in cloud engineering and application development in a way that ensures data security. Get ready to be assisted by a passionate team of data experts to gain an enriching cloud computing experience.
Priyamvada
Author
